
Stay Competitive in a Changing Threat Landscape with Bottomline's Internal Threat Management Solution

Real-Time Analytics
Capture user behavior in real-time across systems

Behavioral Monitoring
Identify high-risk activity and discover bad actors

Machine Learning
Find anomalies and reduce false positive alerts

Multi-App Monitoring
Data from all channels for analysis, reporting and alerts
Get Real-Time Monitoring for Legacy Systems, SaaS, and Web-Based Applications
Non-Invasive and Agent-Less
No agent is put on employee devices. Data is pulled directly from the network into our application. So, whether your organization is remote, hybrid, or bring-your-own-device, you'll have the flexibility to monitor employee actions no matter how your organization is structured.
Spot Anomalies Fast
Speed up investigations by identifying unusual behavior or risks using data enriched by machine learning, analytics and years of experience protecting some of the largest corporations and financial institutions in the world.
Evidence Over Suspicion
Whether an internal threat is malicious or intentional, the details matter! Visually map connections between unusual activities and users, expediting the detection of insider activity, including external fraud initiated from within.
Solutions Designed with an Industry Agnostic Approach


Government

Insurance

Telecom

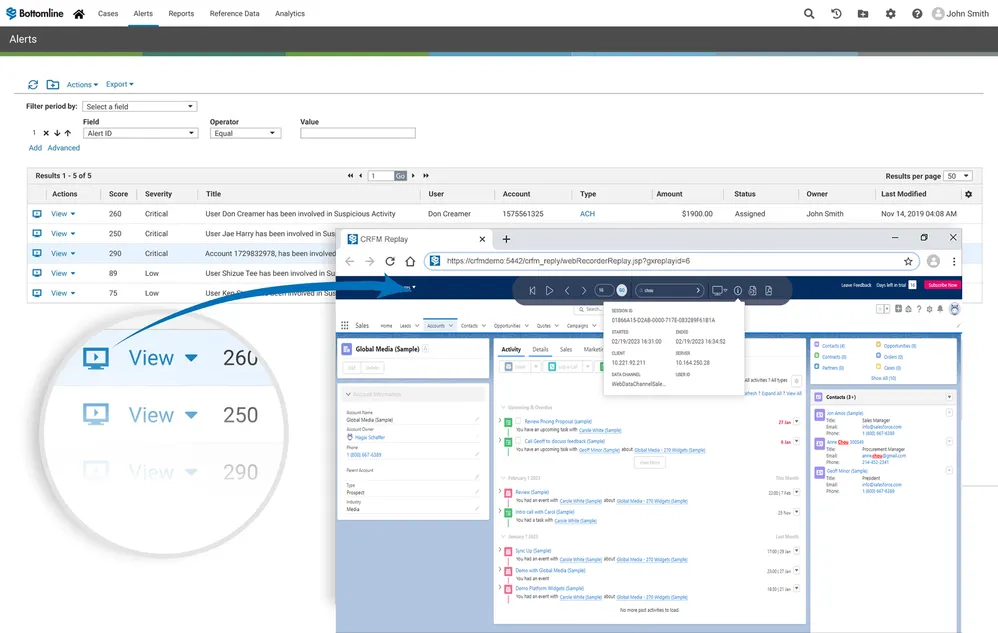
Proactively Monitor Threats Using Intuitive Dashboards and Screens to Ensure Timely Alerts
- View changes to customer and employee accounts
- Holistic view of internal threat alerts across geographies to prioritize investigations
- Identify unusual behavior or risks using data enriched by machine learning, analytics and years of experience protecting some of the largest corporations and financial institutions in the world
- Search cross-platform and across all recorded data
- Quickly expose which users accessed which data
- Search using lists, e.g., VIP names, known fraudulent accounts
- Look across legacy on-premise and SaaS systems in a single search
Leverage a Visual Replay to Take the Guesswork Out of Investigations
Use Bottomline’s Record and Replay functionality to reconstruct user sessions screen-by-screen, allowing your fraud investigators, security officers and internal auditors to view precisely what happened.
-
Ensure recordings are encrypted and secured for future use, including as evidence in court proceedings
-
Run each series of actions through Bottomline’s advanced analytics engine or send them to data lakes or third-party analytics
-
Tailor analytics to identify unauthorized changes to client data, employee policy violations (snooping), and more

"Investigation time decreased by more than 90%."
-U.S. State Criminal Justice Information System (CJIS) Official

For the fourth consecutive year, Bottomline named leader in Insider Risk Management
“With overall strong performance across the parameters of technology excellence and customer impact, Bottomline has been positioned amongst the 2024 technology leaders in the global Insider Risk Management market,”
Aiyaz Ahmed Shaik | Analyst | Quadrant Knowledge Solutions
Take a proactive approach to risk management while removing complexity and enabling compliance

Secure Your Payments
Combat payment fraud and evolving threats in real-time with a SaaS solution that helps you stop fraud before it happens.

Streamline Investigations
Organize, prioritize, and manage investigations by aggregating data from all your risk detection solutions into a centralized tool.

